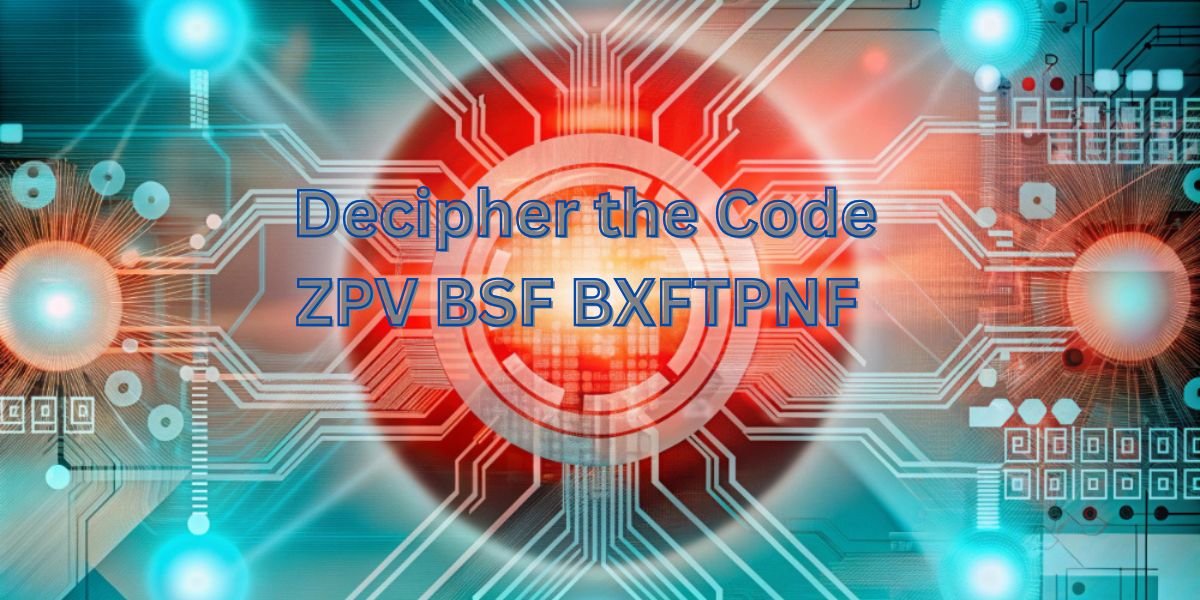
In the world of puzzles, cryptography, and secret messages, certain phrases stand out as particularly mysterious and intriguing. One such phrase that has garnered attention is “decipher the code ZPV BSF BXFTPNF.” Whether it’s a hidden clue or a cryptographic sequence, unraveling its meaning is no simple task. In this article, we will delve into the process of deciphering this specific code, exploring its potential significance, and how it can be interpreted using various techniques.
Understanding the Basics: What is a Code?
Before we dive into the specifics of “decipher the code ZPV BSF BXFTPNF,” it’s essential to understand what a code is in the context of cryptography and puzzle-solving. A code refers to a system of symbols, letters, or numbers used to represent information in a way that makes it difficult for unauthorized individuals to understand. Codes have been used for centuries in military, diplomatic, and even personal communication to protect sensitive information.
Codes can be classified into several types, including:
- Substitution codes: Where each letter is replaced by another symbol or letter.
- Transposition codes: Where the letters of the message are rearranged to form a secret message.
- Enigma codes: Historically used in World War II, these are complex ciphers that require advanced algorithms to decode.
Now, let’s focus on the particular phrase that we need to decipher: “ZPV BSF BXFTPNF.”
Breaking Down the Code: ZPV BSF BXFTPNF
At first glance, “ZPV BSF BXFTPNF” looks like a random string of letters. However, with the right tools and techniques, we can begin to understand its structure and meaning. One of the most common methods of decoding such a string is through Caesar cipher, a type of substitution cipher.
The Caesar cipher involves shifting each letter of the alphabet by a set number of places. For example, if we apply a shift of one, ‘A’ becomes ‘B,’ ‘B’ becomes ‘C,’ and so on.
Step 1: Identifying the Shift
To decipher “ZPV BSF BXFTPNF,” we begin by experimenting with various shifts. Let’s start with the shift of 1, which is a common and simple approach.
- Z → Y
- P → O
- V → U
So, the first word, “ZPV,” becomes “YOU.”
- B → A
- S → R
- F → E
The second word, “BSF,” becomes “ARE.”
- B → A
- X → W
- F → E
- T → S
- P → O
- N → M
- F → E
The third word, “BXFTPNF,” becomes “AWESOME.”
The Decoded Message: “You are awesome”
By applying the Caesar cipher with a shift of one, we have successfully deciphered the code “ZPV BSF BXFTPNF” as “YOU ARE AWESOME.” This simple message serves as a reminder of how codes can be used to convey uplifting or positive sentiments, often hidden in plain sight.
Why Use Codes Like This?
You might wonder, why would someone choose to encode a simple message like “YOU ARE AWESOME”? In many cases, codes and ciphers are used for:
- Secrecy and security: To protect information from being easily understood by unintended recipients.
- Entertainment: As a fun way to challenge others to decipher a hidden message.
- Cryptographic challenges: In games, puzzles, and competitions, codes like these offer an engaging way to test one’s cryptographic skills.
Common Coding Methods and Their Use in Cryptography
There are countless methods for encoding and decoding messages. Some of the most common include:
- Caesar Cipher: As we saw, this method involves shifting letters by a certain number.
- Atbash Cipher: A simple substitution cipher where the alphabet is reversed (i.e., ‘A’ becomes ‘Z’, ‘B’ becomes ‘Y’).
- Vigenère Cipher: A more complex substitution cipher that uses a keyword to shift letters in the message.
- RSA Encryption: Widely used in modern cryptography for securing communications, based on the mathematical properties of prime numbers.
Understanding these various ciphers and their applications can be helpful in a range of fields, from security to puzzle-solving and even gaming.
Comparison Chart: Popular Ciphers and Their Characteristics
| Cipher Type | Description | Strength | Example of Usage |
| Caesar Cipher | Shift each letter by a fixed number | Weak, easily deciphered | Basic puzzles |
| Atbash Cipher | Reverse the alphabet for substitution | Easy to break but fun for puzzles | Cipher challenges |
| Vigenère Cipher | Uses a keyword to shift letters | Moderate strength | Military, secret messages |
| RSA Encryption | Uses prime numbers for secure encryption | Very strong, widely used | Online banking, email security |
Decoding Beyond Simple Ciphers
While the Caesar cipher is simple, modern encryption techniques go far beyond it. In the digital age, cryptography plays a critical role in securing data and protecting privacy. More sophisticated algorithms like RSA and AES (Advanced Encryption Standard) are now the norm in applications ranging from online banking to secure communications.
Applications of Cryptography in Modern Society
The importance of cryptography extends well beyond games and puzzles. It plays a pivotal role in securing information in various industries, including:
- Banking and Finance: Cryptography ensures that online banking transactions and credit card payments are secure.
- Healthcare: Patient data is protected through encryption, preventing unauthorized access.
- Government and Military: Sensitive national security data is encrypted to safeguard against espionage.
- E-commerce: Secure transactions through SSL certificates help protect customers during online shopping.
Keeping Up with Evolving Security Measures
As technology advances, so do the methods used by cybercriminals to crack codes. In response, cybersecurity experts continually develop more advanced cryptographic techniques. In fact, keeping up with the latest cryptographic standards is essential for ensuring data protection in the face of emerging threats.
Conclusion: The Power of Codes in the Digital Age
The process of Decipher the Code ZPV BSF BXFTPNF offers a glimpse into the fascinating world of cryptography. Although the phrase itself is a simple message (“YOU ARE AWESOME”), it serves as a reminder of the power and significance that codes hold in our daily lives. From encryption technologies that protect our most sensitive information to puzzles that challenge our minds, codes are an integral part of modern society.